Cyber Wireless Defense Initiatives are one of the least understood but most important aspect of today’s “connected” business world. In the relatively short time since their inception, cyber-physical systems (CPS) have become ubiquitous in most facets of business and government operations, connecting and supporting applications and infrastructure.
They are used to manage mundane tasks, such as running a factory or office building autonomously, as well as providing critical infrastructure capabilities essential for military operations. This rapid growth and adoption indicates that CPS will be the next technological revolution.
While this paradigm shift is occurring, there has been relatively little attention paid to how vulnerable CPS are to cyber attack.
For example, in February 2021, an unidentified hacker gained remote access to a computer system at a water treatment plant in Florida and increased the amount of sodium hydroxide to nearly 100X its standard levels. Luckily an operator was able to instantly respond and minimize the level, but this event demonstrates the potential for risk that accompany adoption of CPS.
The Problem With Traditional Security Methods
It is imperative that government data is fully secure to prevent threats. Today’s network-based threats require a different security strategy and solution than those based on physical or software barriers, which often stop at either the hardware or encryption level.
Terrorism, foreign government actors, hackers and spies are getting better at accessing government communications and attempts to breach security are increasing. To ensure that data can’t be stolen and influence can’t be exerted over American businesses, the Defense Department needs control of all related devices — including smartphones and personal IoT gadgets connected to wireless networks.
The Evolving State of Cyber Defense Initiatives
There is a growing need for real-time internet traffic analysis to combat the ever-increasing threat of cyber attack. This has led to a new school of thought on traditional network security based around monitoring IoT devices and the data they produce to identify malicious intent or activity.
Cyber defense is moving away from a “black box” approach, where all internet traffic is treated as hostile until deemed safe, to a “white box” model, where devices are scanned before being allowed to connect to government networks.
Existing Mobile Defense
Much of the increased focus on mobile technology is in response to a growing interest in the security of federal networks while federal officials are away from those networks, either at home or abroad.
This increasing emphasis on cyber wireless defense initiatives has led to several proposed network solutions that would keep federal agencies and their data safe while also preventing the theft of sensitive information from malicious entities.
Anonymized Cellular IDs
This approach anonymizes the identity of each mobile device, stopping an attacker in their tracks. It also allows for the identification of rogue devices not associated with any known entity, such as a government or business.
This makes it possible to block GPS-spoofing, which has been used to create disinformation campaigns and confusion during conflicts, or mitigate potential data leaks on vulnerable cellular networks. The anonymized IDs can be paired with the telecommunications company’s existing network data, allowing the government to determine who is using a particular device at a given time.
The Benefits of an Insider Threat Management Approach
By pairing CPS with other insider threat programs that have proven success in deterring and detecting malicious activity, the federal government will be able to improve awareness of suspicious behavior and identify malicious insiders who are seeking to steal data and jeopardize national security.
Deception of Hostile Entities
In addition, the federal government is also moving towards a more proactive model of network defense that monitors information from both within and outside agency networks to detect potential attacks in real-time and respond accordingly.
This provides multiple layers of protection against cyber attacks and a greater chance of mitigating damage before it occurs.
The Ability to Roam Securely in Any Terrain, At Home or Abroad
While many security measures are focused on securing government networks while federal officials are abroad, there is also increasing interest in the ability of our military to operate outside their normal geographic area with a reasonable level of security.
MDM Solutions
Many federal agencies are developing cyber wireless defense management solutions to allow for secure access of sensitive information on both their own and the telecommunication companies’ networks. These solutions will be necessary to implement the anonymized ID approach outlined above.
VPNs
 Additionally, there has been an uptick in the use of Virtual Private Networks (VPNs) to allow personnel access to network resources when officials are away from the office and unable to access these networks directly. These VPNs are increasingly being used in both government and business, although there is also a growing interest in the ability to operate secure systems without using a VPN at all.
Additionally, there has been an uptick in the use of Virtual Private Networks (VPNs) to allow personnel access to network resources when officials are away from the office and unable to access these networks directly. These VPNs are increasingly being used in both government and business, although there is also a growing interest in the ability to operate secure systems without using a VPN at all.
Private APNs
Finally, there is also an interest in the capabilities to operate private Access Point Names (APNs) for military personnel that would not be accessible by malicious parties, but would still allow for secure data transfer via a VPN. This is making it possible to access government networks both on and off base using secured devices without the concern for international security threats.
Security Information and Event Management
Security Information and Event Management (SIEM) solutions are also becoming more commonplace to keep an eye on potential network outages and other potential security concerns.
This allows for a better understanding and viewpoint of all the devices connected to these networks, as well as responding appropriately when unauthorized or corrupt entities attempt to access sensitive information. SIEM is also being used to identify devices that have been compromised, which allows the government to secure these systems before they can be used for malicious purposes.
Protecting Critical Infrastructure
Many federal agencies are also developing plans to protect their critical infrastructure from a cyber threat, particularly when it comes to the use of mobile technologies within those industries.
One of the most notable examples is the United States Nuclear Regulatory Commission, which has an increasing interest in the ability to detect cyber attacks against nuclear power plants and other critical infrastructure while also preventing sensitive information from being stolen.
This amounts to a more robust approach to network defense that is focused on protecting government networks not only while federal officials are located within those networks, but also when they are away from their normal geographic area.
What Is the Future of Cyber Wireless Defense?
There will be a high demand for technology that can identify and maintain secure data traffic at rapid speeds, while keeping both equipment and government data safe from outside threats.
As we enter the next chapter of IoT adoption, defense against cyber attacks will become more crucial and agencies must be prepared to use high tech solutions that can adapt to attacks on the fly and respond accordingly. By preparing for IoT now, the government can ensure citizens’ privacy and security in the future.
Have a need to recruit a C-level, functional leader, or a principal cyber wireless engineer for private or DoD need, consider NextGen’s experience in wireless and cyber security.
 To truly embrace diversity and inclusion in your workplace, you may want to evaluate your company culture.
To truly embrace diversity and inclusion in your workplace, you may want to evaluate your company culture.


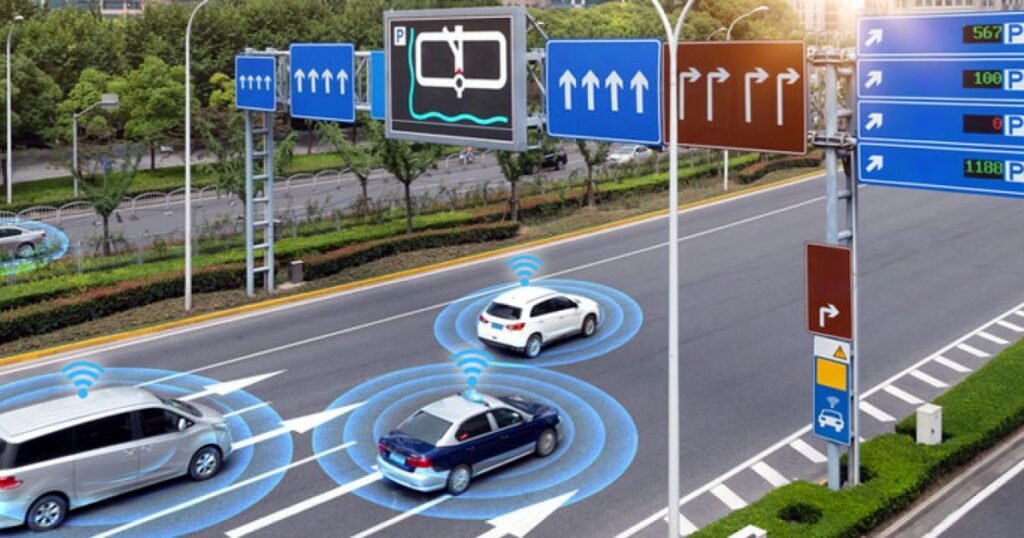 Will autonomous cars and other forms of transportation work without an IOT strategy? The challenge is not the lack of vision for IOT, the major issue is the lack centralized engineering standards and protocols. For an autonomous car to communicate with remote IOT sensors like stop lights, each sensor within the car will need to continued need to be operational and with the most updated software firm to insure predictable operations. The revolution of “Over the Air” software updates in real time became mainstream with the cell phone manufacturers like Samsung
Will autonomous cars and other forms of transportation work without an IOT strategy? The challenge is not the lack of vision for IOT, the major issue is the lack centralized engineering standards and protocols. For an autonomous car to communicate with remote IOT sensors like stop lights, each sensor within the car will need to continued need to be operational and with the most updated software firm to insure predictable operations. The revolution of “Over the Air” software updates in real time became mainstream with the cell phone manufacturers like Samsung 



 Additionally, there has been an uptick in the use of Virtual Private Networks (VPNs) to allow personnel access to network resources when officials are away from the office and unable to access these networks directly. These VPNs are increasingly being used in both government and business, although there is also a growing interest in the ability to operate secure systems without using a VPN at all.
Additionally, there has been an uptick in the use of Virtual Private Networks (VPNs) to allow personnel access to network resources when officials are away from the office and unable to access these networks directly. These VPNs are increasingly being used in both government and business, although there is also a growing interest in the ability to operate secure systems without using a VPN at all.
 On one hand, IoT generated data is sensitive, which impacts regulatory and compliance protocols. Additionally, IoT data is unstructured, complex, frequently anonymized, streams in real-time, and often must be combined from numerous IoT devices – all of which have implications on the existing infrastructure.
On one hand, IoT generated data is sensitive, which impacts regulatory and compliance protocols. Additionally, IoT data is unstructured, complex, frequently anonymized, streams in real-time, and often must be combined from numerous IoT devices – all of which have implications on the existing infrastructure. Organizations today are collecting and integrating IoT data to produce rich customer insights. CX leaders who are looking to future-proof their CX programs are enhancing their data and analytics capabilities and looking to predictive insights to:
Organizations today are collecting and integrating IoT data to produce rich customer insights. CX leaders who are looking to future-proof their CX programs are enhancing their data and analytics capabilities and looking to predictive insights to: